Security is an important, but often overlooked feature when it comes to online giving. In big and small ways, security is a part of every part of the online giving experience.
When we first launched RaiseDonors, there was no way to pre-fill donation forms. As time went by, we evolved to allow parameters to be passed in the URL to pre-fill the various fields on the donation page.
We’ve continuously made a commitment to reduce friction for the donor and for you, the organization.
(Read about reducing friction for your donors using pre-filled donation forms.)
At first, using URL parameters to pre-fill donation forms didn’t seem to cause any problems.
But then it occurred to us — Hey! This could be an asset to a bad person.
As a part of our mission to help you raise donors for your cause, security is always a top priority. So we made our pre-filled donation pages secure with a feature called “Encrypted Parameters.”
The Threat to You and Your Donors
Whenever a donor gives to you online, they have to input what Google calls PII, or Personally Identifiable Information.
Basically, PII is any piece of information that can identify a person. Google defines PII as:
Information that could be used on its own to directly identify, contact, or precisely locate an individual. This includes:
- email addresses
- mailing addresses
- phone numbers
- precise locations (such as GPS coordinates – but see the note below)
- full names or usernames
We reference Google because, chances are, you are using Google Analytics, right? (But even if you aren’t, the same principles apply).
A simple story to explain.
Let’s say you have a list of 10,000 donors you’re planning to reach with an email appeal. Your last campaign had good results, but you’re looking to increase the conversion rate on this campaign.
So you decide to get a bit fancier and customize the landing page by providing some url parameters (described and documented below).
And the beauty is, you can track all of this through Google Analytics reporting!
You specifically decide to help the donor by pre-filling in the donation page with the donor’s contact information. Great!
You send the email and monitor the activity.
Conversion rates are higher than before, and donations are coming in!
You decide this is a new standard for your organization and so you modify your internal process accordingly.
Your IT team has requested that you add some custom Javascript that sends mouse movements to a third-party service.
This allows you to track the donor “hot spots” of mouse activity through heat maps of your website. If a certain section or call-to-action button receives more clicks than another part of your website, it will show up as hotter on the map.
For an added measure, you decide to add Facebook pixel tracking so you can monitor the ad budget on Facebook to see who is converting into donors.
So far, so good. Several months go by.
One of your staff runs a few custom reports in Google Analytics. They notice an odd trend.
The data in the reports contain URL’s that expose PII, Personally Identifiable Information.
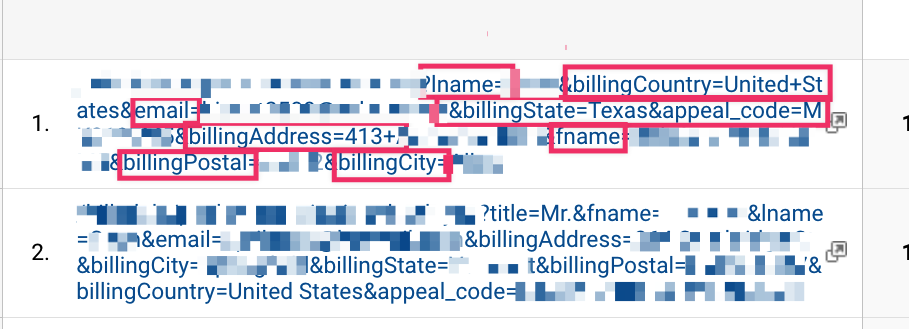
How did PII get sent to Google Analytics?
How widespread is this issue? How can you permanently delete data from Google Analytics?
(By the way, it’s really difficult to permanently delete data from Google Analytics.)
Additionally, you may be in violation of Google’s Terms and Conditions (see section 7).
You will not and will not assist or permit any third party to, pass information to Google that Google could use or recognize as personally identifiable information. You will have and abide by an appropriate Privacy Policy and will comply with all applicable laws, policies, and regulations relating to the collection of information from Visitors.
Google’s Terms and Conditions
To fix this, you’ll need to roll up your sleeves and get creative with your “views” in Google Analytics. But that’s for another article.
And what about your own terms and conditions?
That is information that should stay with your organization alone and never be shared with third parties.
What if your donors found out their contact information was being shared in places that restricted it?
It’s now a compound problem requiring layers of attention.
But the situation gets even worse.
Another few months go by, and you get an anonymous email from “Alex”.
Alex is a malicious user (i.e. a hacker) who has been secretly working in the background. He’s a pro at identity theft. He makes his living by stealing other people’s identity.
The email from Alex explains that he has acquired contact information for 10,000 of your donors and “thought you should know”. More likely, he is asking for ransom money.
A bit far-fetched? Not really. Think about it.
Unintentionally Vulnerable
For the past 6 months, you have been sending the full contact information for all 10,000 of your donors through the Internet.
Those URLs contain the donor’s information in plain text. Even if the data has been sent over SSL/TLS, that doesn’t mean it has been encrypted.
SSL/TLS only encrypts the transmission of the data.
Here are just a few creative ways Alex can harvest your donor’s contact information.
Third-Party Services
If you are using custom JavaScript that contacts third-party services, these parameters are accessible and can be consumed by those third-party services.
Consider Google Analytics, the full URL with supplied parameters would be available in Google Analytics reports.
Consider how many plug-ins work with Google Analytics to scrape data and use it.
Browser Extensions
The URL with all of your donor’s data is available to browser extensions.
Who knows what browser extension your donor has installed or if they are in a public marketplace?
The browser extensions can collect the URL parameters and then share or sell that information to 3rd party sources.
Browser History
The full URL links with all the information can be saved in browser history.
This means malicious code could sweep through a user’s browsing history and extract any information in the URL (contact information, tokens, etc).
Other users of the same browser/computer could also view this information.
Social Shares
Donors may share the donation page link to social media not realizing what they are sharing: a donation form pre-filled with all of their contact information.
Now anyone on Facebook clicking that link has been exposed to that donor’s contact information.
And it’s on Facebook permanently.
This is why RaiseDonor’s social media sharing icons provide a clean URL.
Referrer Header
Anytime a visitor leaves your donation page and heads to any other website, the new website has access to the “referrer” header.
That means the site they land on will have access to all of the parameters in their previous URL.
Those parameters contain all of their PII!
Be Informed
This isn’t intended to be an exhaustive or complete list.
The fact is that hackers have more resources and time on their side than you do. That is their advantage.
Our aim is not to scare you. Our goal is to inform you.
Removing friction points and easing the donation process are the right ways to raise more donors for your organization.
But as those friction points are removed, the door can be opened for malicious users to compromise your process and data.
So, should you stop? NO.
Should you discuss this as a team and evaluate your process and identify any threats and or risks?
Yes, absolutely.
What is RaiseDonors doing about this?
At RaiseDonors, we’ve developed technology that allows you to pre-fill the donation page with your donor’s information in an encrypted and obfuscated way.
We’re extremely excited about our new feature, “Encrypted Parameters,” which I’ll discuss in my next article.
In this article, I’ll explain how URL parameters work and how encrypted parameters help keep donor information safe.
It will be a bit technical, but it will be invaluable for your web or IT department as they strive to keep your information secure.
Today, I just want to leave you with these important thoughts.
First, you need to use technology like RaiseDonors to reduce friction in giving to your donors.
Second, hackers will always be looking for ways to exploit your technology so they can steal donor information.
Lastly, RaiseDonors is working every day to make your online giving platform as secure as possible so hackers can’t get to your donor’s PII.
If you have any questions, please let us know in the comments below. Until then, see you in the next article!


